HTB: MIRAI (10.10.10.48)

Mirai is an easy linux box from hack the box hosting a plex media server and running raspberry pi OS. The raspberry has its default credentials still intact. To escalate privileges, the user pi has the ability to execute sudo commands as root without needing any additional credentials. While this may seem straightforward, there's a twist. The root.txt flag isn't readily available in the root directory. Instead, you have to retrieve the deleted flag from a USB drive attached to the box.
RECON
Nmap
As always we start off with the recon and enumeration process to get an overview of our attack surface and target’s running service.
# Nmap 7.93 scan initiated Mon Oct 2 06:58:37 2023 as: nmap -p- --min-rate 10000 -oA nmap/allports 10.10.10.48
Warning: 10.10.10.48 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.48
Host is up (0.57s latency).
Not shown: 56709 closed tcp ports (reset), 8821 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
80/tcp open http
1993/tcp open snmp-tcp-port
32400/tcp open plex
# Nmap done at Mon Oct 2 07:00:54 2023 -- 1 IP address (1 host up) scanned in 136.62 seconds
# Nmap 7.93 scan initiated Mon Oct 2 07:08:32 2023 as: nmap -sC -sV -p22,53,80,1993,32400 -oA nmap/mirai 10.10.10.48
Nmap scan report for 10.10.10.48
Host is up (0.31s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u3 (protocol 2.0)
| ssh-hostkey:
| 1024 aaef5ce08e86978247ff4ae5401890c5 (DSA)
| 2048 e8c19dc543abfe61233bd7e4af9b7418 (RSA)
| 256 b6a07838d0c810948b44b2eaa017422b (ECDSA)
|_ 256 4d6840f720c4e552807a4438b8a2a752 (ED25519)
53/tcp open domain dnsmasq 2.76
| dns-nsid:
|_ bind.version: dnsmasq-2.76
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
1993/tcp open upnp Platinum UPnP 1.0.5.13 (UPnP/1.0 DLNADOC/1.50)
32400/tcp open http Plex Media Server httpd
|_http-cors: HEAD GET POST PUT DELETE OPTIONS
|_http-title: Unauthorized
|_http-favicon: Plex
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Server returned status 401 but no WWW-Authenticate header.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Oct 2 07:09:08 2023 -- 1 IP address (1 host up) scanned in 36.14 seconds
Given the OpenSSH Version The box is probably running debian 8 jesse.
Port enumeration
TCP Port 53 (DNS)
When DNS listens on TCP it is usually to facilitate zone transfer
Without a valid hostname or domain name I couldint do a zone transfer. I tried guesing from the box name but none worked.
┌─[george@parrot]─[~/HTB/boxes/mirai]
└──╼ $ dig axrf @10.10.10.48 mirai.htb
; <<>> DiG 9.18.16-1~deb12u1~bpo11+1-Debian <<>> axrf @10.10.10.48 mirai.htb
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 16250
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:
;axrf. IN A
;; Query time: 203 msec
;; SERVER: 10.10.10.48#53(10.10.10.48) (UDP)
;; WHEN: Wed Oct 04 05:13:14 EAT 2023
;; MSG SIZE rcvd: 22
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 23761
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; MBZ: 0x0005, udp: 4096
;; QUESTION SECTION:
;mirai.htb. IN A
;; Query time: 4013 msec
;; SERVER: 192.168.252.2#53(192.168.252.2) (UDP)
;; WHEN: Wed Oct 04 05:13:18 EAT 2023
;; MSG SIZE rcvd: 38
nslookup also doesnt tell me much.
┌─[✗]─[george@parrot]─[~/HTB/boxes/mirai]
└──╼ $ nslookup
> server 10.10.10.48
Default server: 10.10.10.48
Address: 10.10.10.48#53
> localhost
;; communications error to 10.10.10.48#53: timed out
Server: 10.10.10.48
Address: 10.10.10.48#53
Name: localhost.localdomain
Address: 192.168.204.129
;; communications error to 10.10.10.48#53: timed out
;; communications error to 10.10.10.48#53: timed out
;; communications error to 10.10.10.48#53: timed out
;; no servers could be reached
> 127.0.0.1
;; communications error to 10.10.10.48#53: timed out
1.0.0.127.in-addr.arpa name = localhost.
>
Port 80
Visiting the page, I see a blank page.
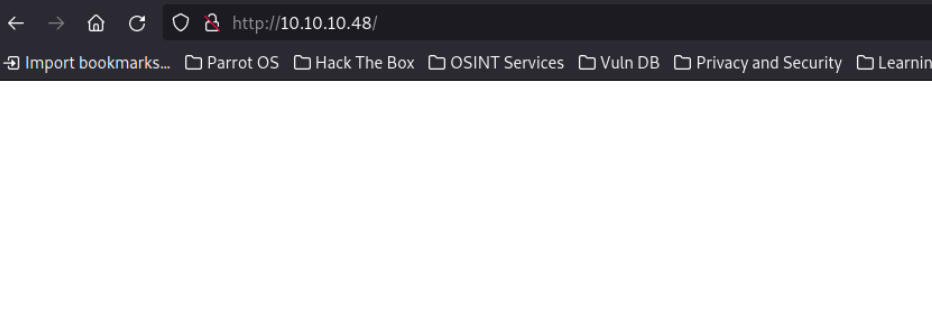
I proxy the request to BurpSuite and note a farmilia header X-Pi-hole which is a DNS sinkhole porpulary associated with raspberry pi. I’ll note that and use it for later.
Directory Bruteforce
I will fire gobuster and bruteforce for directories
┌─[✗]─[george@parrot]─[~/HTB/boxes/mirai]
└──╼ $ gobuster dir -u http://10.10.10.48/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.48/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/10/04 03:47:10 Starting gobuster in directory enumeration mode
===============================================================
/admin (Status: 301) [Size: 0] [--> http://10.10.10.48/admin/]
/versions (Status: 200) [Size: 18]
gobuster Finds two directories and then errors out.
/admin
Admin page redirects to a Pi-hole dashboard page.
Also there is a ‘login’ page but I dont have any credentials to try out. All default credentials dont work.
TCP Port 32400
Visiting this page I come across login page for Plex Server.

Plex Server is a media server kind of like netflix where you set up a server and just upload your media be it movies,series or music and create accounts for people you want to share with to access.
I will register for an account and log in. Nothing intresting so far except for the settings page where I get a version number. The version doesnt do much as I am unable to find an exploit.
Shell as pi
Mirai
According to Cloud Flare, Mirai is a malware that scans the Internet for IoT devices that run on the ARC processor. This processor runs a stripped-down version of the Linux operating system. If the default username-and-password combo is not changed, Mirai is able to log into the device and infect it.
IoT, short for Internet of Things, is just a fancy term for smart devices that can connect to the Internet. These devices can be baby monitors, vehicles, network routers, agricultural devices, medical devices, environmental monitoring devices, home appliances, DVRs, CC cameras, headset, or smoke detectors.
Default credentials
The default credentials for raspberry pi is pi and raspberry. I will try this out and guess what, we are in
┌─[george@parrot]─[~/HTB/boxes/mirai]
└──╼ $ ssh pi@10.10.10.48
pi@10.10.10.48's password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Aug 27 14:47:50 2017 from localhost
SSH is enabled and the default password for the 'pi' user has not been changed.
This is a security risk - please login as the 'pi' user and type 'passwd' to set a new password.
SSH is enabled and the default password for the 'pi' user has not been changed.
This is a security risk - please login as the 'pi' user and type 'passwd' to set a new password.
pi@raspberrypi:~$
Shell as root
Enumeration
Since we have credentials, we can check our sudo privileges.
pi@raspberrypi:~$ sudo -l
Matching Defaults entries for pi on localhost:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User pi may run the following commands on localhost:
(ALL : ALL) ALL
(ALL) NOPASSWD: ALL
At this point I thought wow that was pretty simple. Let me grab the root file and call it a day. Oh how wrong I was.
root@raspberrypi:~# cat root.txt
I lost my original root.txt! I think I may have a backup on my USB stick...
Recovering Deleted data
USB mount on Linux are usually in /media. Using lsblk I can see the raw device is in /dev/sdb
root@raspberrypi:/# lsblk
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT
sda 8:0 0 10G 0 disk
├─sda1 8:1 0 1.3G 0 part /lib/live/mount/persistence/sda1
└─sda2 8:2 0 8.7G 0 part /lib/live/mount/persistence/sda2
sdb 8:16 0 10M 0 disk /media/usbstick
sr0 11:0 1 1024M 0 rom
loop0 7:0 0 1.2G 1 loop /lib/live/mount/rootfs/filesystem.squashfs
The directory has a single file ./damnit.txt and an empty ./lost+found.
Using strings
The strings command looks for printable strings in an object or binary file. A string is any sequence of 4 or more printable characters that end with a new-line or a null character. The strings command is useful for identifying random object files.
I will use strings to try and find if I can see any since I know the flag is a string.
root@raspberrypi:/home/pi# strings /dev/sdb
>r &
/media/usbstick
lost+found
root.txt
damnit.txt
>r &
>r &
/media/usbstick
lost+found
root.txt
damnit.txt
>r &
/media/usbstick
2]8^
lost+found
root.txt
damnit.txt
>r &
3d3e483143ff12ec505d026fa13e020b
Damnit! Sorry man I accidentally deleted your files off the USB stick.
Do you know if there is any way to get them back?
-James
This is just one of the ways to recover the flag.
And thats the box. Thank you all for taking your time to read my blog post, stay tuned for the next!
Happy hacking!